In this second part, we’ll reverse the second unpacking stage of the Cerber sample, and get to the final payload. We’ll be dealing with some binary protections, custom structures, and process injection. Let’s get started !
Latests posts :
Reversing Cerber VB packer – Part 1 : shellcode extraction
In this post series, we are going to fully reverse the inner working of a Visual Basic packer, used at least by some Cerber ransomware sample. My whole methodology, meaning each and every step I took, will be documented here. We’ll end up with a complete view of the whole unpacking process before the actual payload is started, and I hope it will help you learn to do this on your own !
Reversing a shellcode with import by hash
A few days back a fellow reddit user asked if a powershell command he found was malicious … I checked, and here is the result ! (spoiler alert : of course if was)
Continue reading
Disable Windows Defender in powershell – a script to finally get rid of it
Once again, after a Windows update, Windows Defender activated itself again. It finally bothered me enough to take an actual look at how to disable it permanently and reliably, in a fully automated way (a PowerShell script), on my Windows 10 20H2 (build 19042).
IDA PRO life easier : a python plugin turning function parameters to enum values
As an introduction to IDA python, we’re going to write a script that turns immediate values function parameters into enum values. It is a very common things to do, and a simple python script can handle it in most cases. So let’s make our lives easier with some python !
Windows PEB parsing – A binary with no imports
We’re going to see how a program can parse the PEB to recover Kernel32.dll address, and then load any other library. Not a single import is needed !
Solving an IDA Bug – struct list with blank elements
The other day, I encountered an isse with IDA pro 7.5: my struct and enum list left panel became empty, with blank elements. As you can see belo, It was unusable:
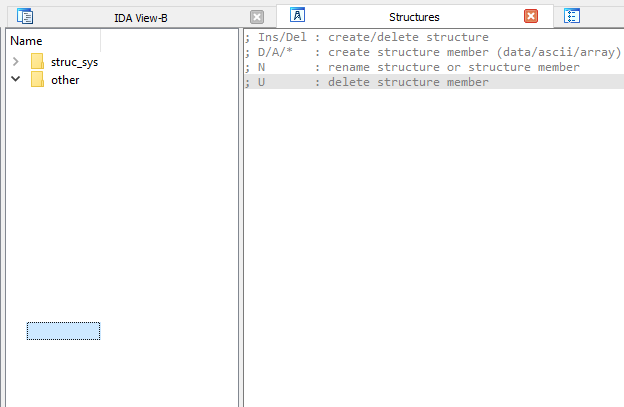
I have no idea how this happended exactly. IN the end I had to contact the support, and here is their solution, a single python commnd:
import ida_netnode
ida_netnode.netnode("$ dirtree/structs").kill()
You can then save and reopen the idb, the list should have been updated and be fine. You’ll lose the folders though, but it’s not that long to do so it’s ok.
This command also works with enums instead of structs, and maybe other pannels like this.
Writing a PE packer – Part 5 : simple obfuscation
In this tutorial, we are going to complete our packer with some very basic obfuscation, as a demonstration of the possibilities we have.
Writing a PE packer – Part 4 : packing with no relocation
At the end of the last part, I drawed your attention toward the fact that Mingw32 doesn’t produce movable binaries: it cannot create relocation table. You can force it to put the “Dll can move” flag, but without a relocation table, this binary would not work. We are going to change our packer to handle such non movable binaries.
Writing a PE packer – Part 3 : packing with python
We have everything ready to do the actual packing of an ASLR enabled PE32 file. We’ll turn our loader in an unpacking stub, and use python to create a packed binary.
